AAA
AAA is something I use fairly often, I'll just post a sample config and some verification steps.
Basic Configuration
ip tacacs source-interface mgmt0
tacacs-server host 10.10.209.99 key 7 "fewhg123!"
aaa group server tacacs+ MY-TACACS
server 10.10.209.99
use-vrf management
source-interface mgmt0
aaa authentication login default group MY-TACACS
aaa authentication login console local
N7K-1# test aaa group MY-TACACS gregg XXXXXXXX
user has been authenticated
Accounting
aaa accounting default group MY-TACACS
Authorization
I really doubt that authorization with be on the lab (it would be a real bear without access to the ACS server and this isn't a security test). Anyway, here is a basic config
aaa authorization config-commands default group MY-TACACS
aaa authorization commands default group MY-TACACS
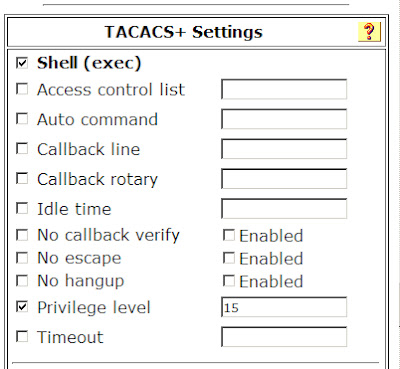
On my ACS server (I'm running the old 4.2 as a VM in my lab), I added the shell to the user screen via the interface menu:
Then I went to the user and allowed shell access with privilege level 15:
Here is a command failing authorization before the change:
N7K-1# sh log
Error: AAA authorization failed AAA_AUTHOR_STATUS_METHOD=16(0x10)
Here is a command passing authorization after the change:
N7K-1# sh log
Logging console: enabled (Severity: critical)
Logging monitor: enabled (Severity: debugging)
Logging linecard: enabled (Severity: notifications)
SNMPV3
SNMPV3 uses message integrity, authentication and encryption to secure SNMP.
The security level and models listed below were taken from the NX-OS management guide
Security Levels
The security level determines if an SNMP message needs to be protected from disclosure and if the
message needs to be authenticated. The various security levels that exist within a security model are as
follows:
• noAuthNoPriv—Security level that does not provide authentication or encryption.
• authNoPriv—Security level that provides authentication but does not provide encryption.
• authPriv—Security level that provides both authentication and encryption.
Security Models
Basic SNMPV3 Configuration
snmp-server contact gregg@hellanetwork.com
snmp-server community public group network-operator
snmp-server user TEST network-operator auth md5 0x23f5c72c424a51e873f1401d272482cc priv 0x23f5c72c424a51e873f1401d272482cc localizedkey
snmp-server user admin network-admin auth md5 0xf09b00c690cd35dbbb6744db828f49ae priv 0xf09b00c690cd35dbbb6744db828f49ae localizedkey
snmp-server host 10.10.209.250 version 2c public udp-port 1163
snmp-server host 10.10.209.60 version 2c public udp-port 2162
snmp-server host 10.10.209.60 version 3 auth TEST
snmp-server enable traps license
IP ACLs, MAC ACLs and VLAN ACLs
Nothing very special but I will use the session manager to show a few configurations.
N7K-1# configure session ACL
Config Session started, Session ID is 1
Enter configuration commands, one per line. End with CNTL/Z.
IP ACL
N7K-1(config-s)# ip access-list TEST
N7K-1(config-s-acl)# permit ip an any ?
<CR>
dscp Match packets with given dscp value
fragments Check non-initial fragments
log Log matches against this entry
packet-length Match packets based on layer 3 packet length
precedence Match packets with given precedence value
time-range Specify a time range
IP Objects
N7K-1(config-s)# object-group ip address TEST
N7K-1(config-s-ipaddr-ogroup)# host 1.1.1.1
N7K-1(config-s-ipaddr-ogroup)# 2.0.0.0/8
Time-Range
N7K-1(config-s)# time-range TEST-TIME
1 periodic Friday 17:00:00 to Monday 08:00:00
Verify and Commit Session
N7K-1(config-s)# verify
Verification Successful
N7K-1(config-s)# commit
Commit Successful
MAC ACL
7K-1(config)# mac access-list MAC-TEST
N7K-1(config-mac-acl)# 1 permit beef.beef.beef ffff.ffff.ffff any
Applying the MAC ACL to an Interface
N7K-1(config-if)# mac port access-group MAC-TEST
VACL
N7K-1# conf session VACL
N7K-1(config-s)# vlan access-map VACL-TEST 1
N7K-1(config-s-access-map)# match ip address TEST
N7K-1(config-s-access-map)# match mac address MAC-TEST
N7K-1(config-s-access-map)# action drop
N7K-1(config-s-access-map)# verify
Verification Successful
N7K-1(config-s)# commit
Commit Successful
Port Security
Port security has three modes; static, dynamic and sticky. Sticky address are stored in NVRAM so that they are permanent.
I'll add details to Port Security when I do my next PEC lab.
DHCP Snooping
Need a PEC lab
Dynamic ARP Inspection
Need a PEC lab
IP Source Guard
Need a PEC lab
TrustSEC
Need a PEC lab